NOMA - How successive interference cancellation (SIC) works?
NOMA uses power domain multiplexing of users sharing same time and frequency resources. This is accomplished by performing superposition coding at the transmitter and successive interference cancellation (SIC) at the receiver. In the previous post, we saw a graphical view of superposition coding. In this post, we will see how SIC is carried out to decode the superposition coded signal at the receiver side.
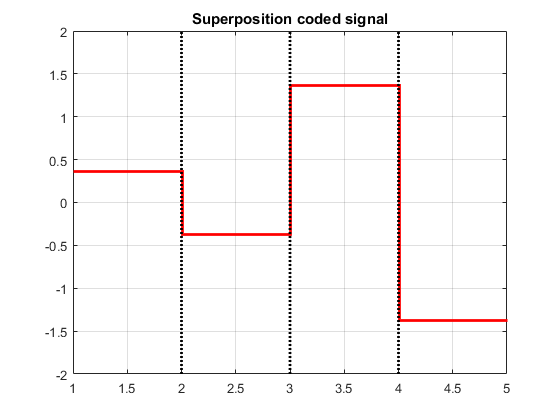
As a quick recap, we had two users with data x1 and x2 respectively. (What if we had more than two users?) We first did BPSK modulation to both x1 and x2. Then we obtained the superposition coded signal as x = √a1x1 + √a2x2 where, a1 and a2 are the power weights given to x1 and x2 respectively, such that, a1 + a2 = 1. We took an example of x1 = 1010 and x2 = 0110. After BPSK modulation and choosing a1 = 0.75 and a2 = 0.25, we obtained the superposition coded signal x, as shown below:
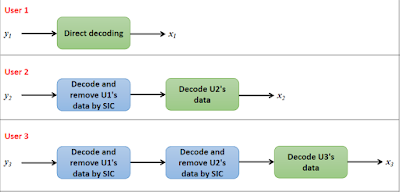
Before decoding, let us take a look at SIC algorithm. SIC is an iterative algorithm where data is decoded in the order of decreasing power levels. That is, data corresponding to the user who is given the highest power is decoded first, then the data of the user who is given the next highest power is decoded. This process repeats till we have decoded all user's data. For our simple case of two user NOMA system, the steps involved in SIC are described below:
- Step 1: Directly decode x to get the signal that is weighed with high power. For example, if x1 is given more weight, (i.e., a1 > a2), direct decoding of x gives x1.
- Step 2: Multiply the signal decoded in step 1 by its corresponding weight and subtract it from x.
For example, if x1 is decoded in the previous step, subtract √a1x1 from x. This would give us, x - √a1x1. - Step 3: Decode the signal obtained in step 2 to get the other signal which was multiplexed with low power.
For example, decoding of x - √a1x1 obtained from the previous step would yield us x2
These steps may appear pretty foggy, but please bear with me as we follow through our example to prove for ourselves that the SIC algorithm indeed works nicely.
Now, let's apply SIC to our example step by step. (Here, we've made a perfect SIC assumption. To see what happens when SIC is imperfect, see this post). Recall from the previous post that we chose values for power weights as a1 = 0.75 and a2 = 0.25. This means that we have given x1 more power weight that x2. So, following step 1, when we do direct decoding of x, we would get x1.
What do we mean by direct decoding? In our case, we have used BPSK modulation at the transmitter side. So what we mean by direct decoding is that, we are going to apply BPSK demodulation directly to x.
We might think that we would run into trouble because know that x contains a linear combination of x1 and x2, which are two different messages. But we will see shortly that SIC handles this problem very nicely. So let's go ahead and perform BPSK demodulation on x.
BPSK demodulation is basically, a simple thresholding. Let's set the threshold to zero. For each symbol, if the amplitude exceeds zero, we are going to decode it as 1, and 0 otherwise.
This is a plot of x, and the threshold is denoted as a solid black horizontal line. Let's decode x symbol by symbol. We observe that the first and third symbols lie above the threshold of zero. So, we make the decision that the first and third transmitted bits are ones. The second and fourth symbols lie below the threshold. So, we make the decision that the second and fourth transmitted bits are zeros. Thus, the decoded sequence in order is 1010. Which is the same as x1!
In other words, we arrived at x1 by directly performing BPSK demodulation on x, totally ignoring the fact that x had a component of x2 too. This was possible because, we allocated a higher power weight to the x1 component of x. Thus the presence of the other component x2 in x can be safely ignored. In other words, we treat x2 as interference and ignore it.
We've completed step 1 of SIC process. What is the intuition behind the next two steps of SIC?
We know x = √a1x1 + √a2x2. The values of √a1 and √a2 are known to as because they are design choices. Further, we obtained x1 by following step 1. So if we subtract √a1x1 from x, we will be left with √a2x2. From √a2x2, it is pretty much easy to obtain x2.
Let's move on to step 2.We have to multiply the x1 component by its corresponding power weight and subtract it from x. We have to be careful now. We have obtained x1 to be 1010. But x1 is present in x in its BPSK modulated form. In other words, x does not contain x1 as 1010. x contains x1 as 1 -1 1 -1, which is the BPSK modulated version of 1010. So, we have to subtract this BPSK modulated version of x1 component from x. After subtraction, the graph would look like this.
Notice that this looks similar to the graph which shows scaled data of user 2 in the previous post.
We are done with step 2. Moving on to step 3. After subtraction, we simply have to demodulate the resulting signal using BPSK rule as before. Following BPSK rule, we see that the first and fourth symbol would be demodulated as zeros and the other symbols would be demodulated as ones. Thus, the demodulated signal, put in order is 0110, which is same as x2.
This and the previous post are written just to prove for ourselves that NOMA indeed works as intended. We have successfully multiplexed two separate data in the power domain and recovered it. We have considered a perfectly ideal case by not including channel noise effects etc., Our goal here is just to understand how NOMA works. We will see the BER performance of NOMA in the presence of AWGN in the following posts. Thank you.
PS: Click here to download the complete MATLAB code for NOMA with superposition coding and SIC.
This is just a toy example to understand the concept of NOMA. In the next post, we will see how to simulate a NOMA system and plot its bit error rate (BER) using MATLAB.
Reference:
This is an excellent paper which explains the basics of NOMA for starters.
Y. Saito et al., Non‐orthogonal multiple access (NOMA) for cellular future radio access, IEEE 77th Vehicular Technology Conference (VTC Spring) (Dresden, Germany), 2013, pp. 1-5.
Next post: How to simulate a simple NOMA system using MATLAB



How to perform mobile edge computing using NOMA?
ReplyDeleteHi Satarupa, in mobile edge computing, the users have to communicate with the server to perform task offloading. For this communication NOMA can be used. Like, multiple users can use the same carrier to offload their tasks to the server.
DeleteThank you Joe. This blog is really helpful. Could you please share more on cooperative NOMA ????
DeleteHi Satarupa,
DeleteGlad to know that you found the blog useful.
Sure! We will see more on cooperative NOMA in future posts
really,this blog is useful Mr. Joe... we r glad to seee your next post. if u r dealing with secrecy rate of NOMA??
DeleteHello dear,can you help in writing NOMA code user pair association to base station .
ReplyDeleteHi! We will see about user pairing in a future post
DeleteHi joe,
ReplyDeleteWhy don't you calculate the channel gain at two users?
Hi, this post focuses only on the basic skeletal operation of SIC. Channel gain was included in the succeeding posts
DeleteCan you do a tutorial for parallel inteference cancellation for NOMA ?
ReplyDeleteHi Minh, Thanks for the suggestion, will make a post about that soon!
DeleteTHank you, much appreciated the effort.
DeleteHello sir, can you please upload code for NOMA in V2V communication?
ReplyDeleteHi, thanks for the suggestion. We'll cover V2V NOMA in a future post!
DeleteHi, Will you please tell: Have you done something relevant to Codeword-level SIC in NOMA?
ReplyDeleteplease help code for PARP reduction of OFDM based NOMA
ReplyDeletehello can you help me in noma with polar code in matlab ??
ReplyDeleteHi Joe, Can I ask your permission to translate your writing regarding NOMA into Vietnamese, I will add full credit of your work. Thank you very much !
ReplyDeleteHi Minh, That's great! Go ahead :)
DeleteIf you are planning to make it available online, do share your link with me. I'll give a shoutout to you here in the blog!
DeleteHello can u write post about Power Domain NOMA ?
ReplyDeleteHello Joe. Assuming the transmission is done over Rayleigh Fading channel, will the SIC operation differ from the above? If no, where will the channel (gain) be placed in the SIC operations that you have outlined above?
ReplyDeleteHi, Joe! How does the receiver knows the decoding order and power allocation coefficients?
ReplyDeleteHi Travis, those information are conveyed prior to data transmission through a control channel
DeletePlease Post IRS in NOMA by considering Rayleigh fading
ReplyDelete